Data Breach Response Plan
Home »
The passage of the Privacy Amendment (Notifiable Data Breaches) Act 2017 established a Notifiable Data Breaches (NDB) scheme in Australia. Commencing from 22 February 2019, the NDB scheme requires organisations covered by the Australian Privacy Act 1988 (the Act) to notify any individuals likely to be at risk of serious harm by a data breach. The notice must include recommendations about the steps individuals should take in response to the data breach, including notifying the Australian Information Commissioner.
1 Introduction
1.1 What is a data breach?
A data breach occurs when personal information is lost or subjected to unauthorised access, modification, use or disclosure or other misuses. Personal information is information or an opinion about an identified or reasonably identifiable individual. Data breaches may include (but are not limited to):
- Unauthorised access by a third party,
- Information accidentally being uploaded to a public website or a laptop or USB drive containing personal information being lost or stolen and can be caused by or exacerbated by a variety of factors, affect different types of personal information and give rise to a range of actual or potential harms to individuals, agencies or organisations.
1.2 Which data breaches are notifiable?
Not all data breaches require notification. The Notifiable Data Breaches (NDB) scheme only requires organisations to notify when there is a data breach that is likely to result in serious harm to any individual to whom the information relates. The purpose of this plan is to enable that assessment to be undertaken and for Approach Services to meet its reporting obligations. Where a data breach is assessed as having occurred, the Data Breach Response Team will take immediate action.
1.3 Data breach response plan
This data breach response plan outlines definitions and sets out procedures and clear lines of authority for Approach Services' staff if Approach Services experiences a data breach or suspects that a data breach has occurred.
This response plan is intended to enable Approach Services to contain, assess and respond to data breaches in a timely fashion and help mitigate potential harm to affected individuals. It sets out contact details for the appropriate staff in the event of a data breach, clarifies the roles and responsibilities of staff, and documents processes to assist Approach Services to respond to a data breach.
2 Data breach response team
The purpose of having a Response Team is to ensure that the relevant staff, roles and responsibilities are identified and documented before the data breach happens. Different skill sets and staff may be needed to respond to one breach compared to another. The Response Team has the authority to take the necessary steps in the event of a breach without the need to seek permissions, particularly in time-critical scenarios.
2.1 Response team membership
Sam Sayem, Response Team Lead
- Ensures the team stays focused on reducing damage, recovering swiftly, and functioning efficiently by coordinating response actions' overall direction and strategy.
Eva Sayem, Communication Lead
- Manages the incident response's relevant internal and external communications. It may be necessary to communicate across an organisation's teams and divisions and with external stakeholders.
Ilana Borsje, Investigation Lead
- Coordinates efforts to determine the cause of an incident. It's critical to collect as much valuable data as possible, specifically if the knowledge can help resolve an immediate problem and prevent future problems.
John Espiritu, Documentation Lead
- Keeps track of incident response activities and measures for reference.
Legal Staff, Legal Representation Lead
- Ensures that incident response actions are carried out according to applicable rules and regulations to protect the organisation.
3 Assessing suspected data breaches
If any Approach Services staff member suspects or becomes aware of a data breach, this plan is activated and must be followed. The plan requires a reasonable and expeditious assessment to determine if the data breach will result in serious harm. The following chart outlines the staff roles involved in assessing a data breach.
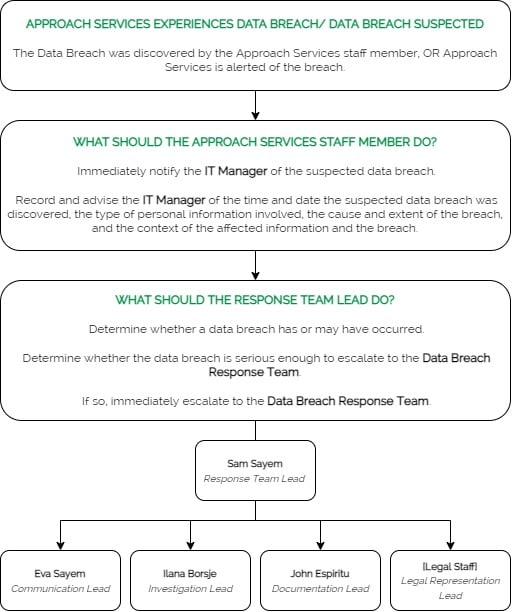
3.1 When should the IT Manager escalate a data breach to Approach Services data breach response team?
3.1.1 IT manager to use discretion in deciding whether to escalate to the response team.
Some data breaches may be comparatively minor and can be dealt with quickly without action from the Data Breach Response Team.
In determining whether to escalate data breaches to the Response Team, the IT manager should consider the following questions:
- Are multiple individuals affected by the breach or suspected breach?
- Is there (or may there be) a real risk of serious harm to the affected individual(s)?
- Does the breach or suspected breach indicate a systemic problem in Approach Services processes or procedures?
- Could there be media or stakeholder attention resulting from the breach or suspected breach?
If the answer to any of these questions is yes, it may be appropriate for the IT manager to notify the rest of the Response Team.
3.1.2 IT manager to inform the Response Team Coordinator of minor breaches.
If the IT manager decides not to escalate a minor data breach or suspected data breach to the Response Team for further action, the IT manager should:
- send a brief email to the Response Team Lead that contains the following information:
- description of the breach or suspected breach
- action that was taken by the IT manager or Approach Services officer to address the breach or suspected breach
- the outcome of that action, and
- the IT manager's view that no further action is required
- save a copy of that email in the following folder:
- Nextcoud > 6. IT > Data Breach > Documentation
4 Data breach response process
There is no single method of responding to a data breach. Data breaches must be dealt with on a case-by-case basis by assessing the risks involved and using that risk assessment to decide the appropriate course of action.
There are four key steps to consider when responding to a breach or suspected data breach.
STEP 1: Contain the breach and do a preliminary assessment
STEP 2: Evaluate the risks associated with the breach
STEP 3: Notification
STEP 4: Prevent future breaches
The Response Team should ideally undertake steps 1, 2 and 3 either simultaneously or in quick succession. Refer to the detailed checklist at the end of this plan.
Depending on the breach, not all steps may be necessary, or some steps may be combined. In some cases, it may be appropriate to take additional measures specific to the nature of the breach. The checklist is intended to guide the Response Team in a data breach and alert the Response Team to a range of considerations when responding to a data breach.
4.1 Evaluating a serious risk of harm to an individual
In evaluating whether there is a serious risk of harm to an individual whose information is the subject of a data breach; the Response Team must consider:
- what type of personal information is involved (and in particular, whether it is sensitive information);
- whether any protections would prevent the party who receives (or may have received) the personal information from using it (for example, if it is encrypted);
- the nature of the harm that could arise from the breach, for example, whether an individual was reasonably likely to suffer:
- identity theft;
- financial loss;
- a threat to their physical safety;
- a threat to their emotional wellbeing;
- loss of business or employment opportunities;
- humiliation, damage to reputation or relationships; or
- workplace or social bullying or marginalisation;
- what steps have been taken to remedy the breach (and how certain Approach Services is that they are effective)?
4.2 Notifying the individuals affected
As soon as reasonably practical after Approach Services has submitted the statement to the Office of the Australian Information Commissioner (OAIC), Approach Services must:
- if practical, take reasonable steps to notify the contents of the statement to each of the individuals to whom the information relates; or
- if practical, take reasonable steps to notify contents of the statement to each of the individuals who are at risk from the eligible data breach.
Suppose it is not practical to undertake either of the above. In that case, the Response Team must ensure a copy of the statement is published on Approach Services' website, and reasonable steps are taken to publicise the contents of the statement (for example, by notifying its members).
4.2 Records management
Documents created by the Response Team should be saved in the following folder:
- Nextcoud > 6. IT > Data Breach > Documentation

